In the mid to late 2000s, as cloud technology was being adopted, Cloud computing was primarily a software as a service. As cloud technology evolved into a platform and infrastructure services, the security of assets/services/processors being run on the cloud, became a significant hurdle to the adoption of the cloud. Now, cloud services have evolved into a more hybrid ecosystem with a wider attack surface. As the use of data and vital services run in the cloud increases, so has the nature and number of threats faced by enterprises. Therefore, security has become an essential component of a well-conceived cloud strategy.
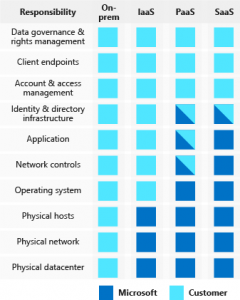 It is a common misconception that security in the cloud is a service that can be outsourced completely to the cloud provider. Security in the cloud is a joint venture between the owner/builder of the assets and the cloud service provider. Figure 1 is a guideline on how this responsibility is shared within Azure. This is why its important for an architect to:
It is a common misconception that security in the cloud is a service that can be outsourced completely to the cloud provider. Security in the cloud is a joint venture between the owner/builder of the assets and the cloud service provider. Figure 1 is a guideline on how this responsibility is shared within Azure. This is why its important for an architect to:
- Understand the security concepts and capabilities within a cloud environment.
- What tools are available to secure and monitor your environment.
- What tools and capabilities are there to address the attacks and threats.
Throughout my time working in Azure, I have seen the development of Azure Security Center from a preview service, to an essential tool in the management of Azure. Before diving into the tool itself, it’s important to understand that the Security Center is only a single tool, out of many that can assist in maintaining security. There also exist some fundamental security concepts that need to be understood first to build securely in the cloud.
Defense in depth.
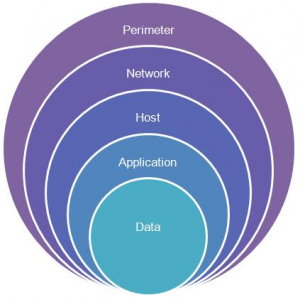 This approach removes reliance on any single layer of protection and acts to slow down an attack and provide alert telemetry that can be acted upon, either automatically or manually at each layer using a number of different tools. It also enables you to build a cloud strategy that addresses each layer separately in the areas of protection, detection, and mitigation of a threat. Bellow, I will address several basic features and concepts that you should be aware of in regards to security.
This approach removes reliance on any single layer of protection and acts to slow down an attack and provide alert telemetry that can be acted upon, either automatically or manually at each layer using a number of different tools. It also enables you to build a cloud strategy that addresses each layer separately in the areas of protection, detection, and mitigation of a threat. Bellow, I will address several basic features and concepts that you should be aware of in regards to security.
Identity and Access
Azure AD & MFA
In a mobile-first world, no longer is the network the primary security parameter. Identity, access, and authentication on BYOD devices have made them the new security vulnerability.
Azure Active Directory (AD) is Azures cloud-based identity service. With built-in support for synchronizing with your existing on-premises Active Directory or to be used as a stand-alone identity manager.
Azure active directory additionally acts as a secure single sign-on service. This means that all your applications, whether on-premises, in the cloud or even mobile can share the same credentials. By using a centralized identity provider, you’ll have centralized the security controls, reporting, alerting, and administration of your identity infrastructure.
Multi-factor authentication (MFA) provides an additional layer of security for your identities by requiring two or more elements for full authentication. These elements fall into three categories:
- Something you know
- Something you possess
- Something you are
Azure AD has MFA capabilities built in and will integrate with other third-party MFA providers. It’s provided free of charge to any user who has the Global Administrator role in Azure AD. All other accounts can have MFA enabled by purchasing licenses with this capability — as well as assigning a license to the account.
Identities to services and applications.
in an enterprise environment, authentication is not only necessary between applications and users but across applications. Azure AD provides this service using two methods:
- Service principals
- Managed identities for Azure services.
Service principles are the harder of the two to manage. A managed identity can be instantly created for any Azure service that supports it in your Azure Ad tenant. The Azure infrastructure will automatically take care of authenticating the service and managing the account. You can then use that account like any other Azure AD account, including securely letting the authenticated service access other Azure resources.
Role-based access control
Role-based access control is a privilege management system within the portal. Identities are mapped to roles directly or through group membership, with the option of creating custom roles with access to specific permissions on resources, and resource providers.
Administrators are able to ensure the minimum necessary permissions are granted to Azure assets. RBAC is more geared for management of the portal and admin access to resources rather than user management for application or end users.
Privileged Identity Management
In addition to managing Azure resource access with role-based access control (RBAC), Privilege Identity Managment provides a comprehensive approach to infrastructure protection by including the ongoing auditing of role members as their organization changes and evolves. Azure AD Privileged Identity Management (PIM) is an additional, paid-for offering that provides oversight of role assignments, self-service, and just-in-time role activation and Azure AD and Azure resource access reviews.
Data Security – Encryption.
There are two primary types of data encryption, symmetric and asymmetric. similarly, there are two types of data that need to be protected. Data at rest and data in transit.
Symmetric encryption uses the same key to encrypt and decrypt the data. Asymmetric encryption, on the other hand, uses a public key and private key pair. Either key can encrypt but a single key can’t decrypt, you need the paired key to do so. for example Asymmetric encryption is used for Transport Layer Security (TLS) (used in HTTPS) and data signing. Both symmetric and asymmetric encryption plays a role in properly securing your data.
Encrypt raw storage
Azure Storage Service Encryption helps you protect your data to meet your organizational security and compliance commitments. With this feature, the Azure storage platform automatically encrypts your data before persisting it to Azure Managed Disks, Azure Blob storage, Azure Files, or Azure Queue storage, in a storage account and decrypts the data before retrieval. The handling of encryption, encryption at rest, decryption, and key management in Storage Service Encryption is transparent to applications using the services. It allows for authorized applications to still access the data when necessary keys are presented.
While data at rest would only be a vulnerability if the hardware storage was to be compromised, these encryption criteria are necessary for data compliance and regulatory requirements. Industry and government regulations such as HIPAA, PCI, and FedRAMP, have specific encryption requirements.
Encrypt virtual machines
Azure Disk Encryption (ADE) encrypt your Windows and Linux IaaS virtual machine disks. Azure Disk Encryption utilizes BitLocker feature on Windows and the dm-crypt feature of Linux to provide volume encryption for the OS and data disks attached to a virtual machine. The solution is integrated with Azure Key Vault to help you control and manage the disk encryption keys and secrets. There are specific parameters on the specifics of ADE and ADE can be enabled on scaling scenarios for Windows and Linux virtual machines.
Databases Encryption
Transparent data encryption (TDE) encrypts Azure SQL Database and Azure Data Warehouse Data. The database, associated backups, and transaction log files at rest are encrypted and decrypted in real-time without requiring changes to the application.
TDE encrypts utilizes symmetric key called the database encryption key. By default, You have two options with key management for TDE. Azure provides a unique encryption key per logical SQL Server instance and handles all the details. Bring your own key (BYOK) is also supported with keys stored in Azure Key Vault.
Securing encryption keys, passwords connection strings, and other sensitive information.
Azure Key Vault is a cloud service that works as a secure secrets store. Key Vault can contain multiple secure containers, called vaults that are backed by hardware security modules (HSMs). Azure Key Vault can handle requesting and renewing TLS certificates, providing the features required for a robust certificate lifecycle management solution. Key Vault is designed to support any type of secret. These secrets could be passwords, database credentials, API keys, and certificates.
Because Azure AD identities can be granted access to use Azure Key Vault secrets, applications with managed service identities enabled can automatically and seamlessly acquire the secrets they need.
Azure Networking and Azure Virtual Networking.
There are many tools and techniques for achieving network security in Azure. They are mostly dependant on the network configuration, architecture and assets deployed to the network. I will limit the information I present here in regards to network security to a relatively new feature in Azure, Azure DDoS Protection
DDoS protection in Azure always existed to some extent. But customers did not always have transparency in the technology and the method of protection till recently. Now Azure provides protection on two tiers. A free basic tier and a standard tier, to better protect Azure assets from DDoS attacks.
In the Standard tear, dedicated traffic monitoring and machine learning algorithms are used to apply policies to public IP addresses associated to resources deployed in virtual networks. These resources could be Azure Load Balancer, Azure Application Gateway, and Azure Service Fabric instances, with the exception of App Service Environments.
Azure monitor allows you to monitor attacks in real time with Real-time telemetry data. Rich attack mitigation analytics are available via diagnostic settings. Application layer protection can be added through the Azure Application Gateway Web Application Firewall or by installing a 3rd party firewall from Azure Marketplace.
Mitigation
When actual traffic utilization exceeds the thresholds defined in the DDoS Policy, mitigation is applied to the traffic. Then it is redirected and a 3-factor check is performed on the traffic data.
- Ensuring packets conform to internet specifications and are not malformed.
- Interact with the client to determine if the traffic is potentially a spoofed packet (e.g: SYN Auth or SYN Cookie or by dropping a packet for the source to retransmit it).
- Rate-limit packets, if no other enforcement method can be performed.
Azure Security Tools
Below are a few tools that are available in Azure to monitor and aid in securing your Azure resources.
- Azure Security
- Access Review
- Azure Ad Privileged identity management
- Azure Security Center
- Azure information Protection
- Azure Advisor
It is important to note that the information listed above is only the tip of the iceberg in regards to security in Azure. Comprehensive steps need to be taken, to plan and protect the resources you build and the services you utilize in Azure.
